Here's how the instructions in BUYUNLOCKCODE.txt file read:
Hi, your ID = XXXXX
All important files were encoded with RSA-1024 encryption algorithm.
There is the only way to restore them - purchase the unique unlock code.
Warning! Any attempt to recovering files without our "Special program" will cause data damage or complete data loss.
As we receive your payment, we will send special program and your unique code to unlock your system.
Guarantee: You can send one of the encrypted file by email and we decode it for free as proof of our abilities.
No sense to contact the police. Your payment must be made to the e-wallet. It's impossible to trace.
Don`t waste your and our time.
So, if you are ready to pay for recovering your files, please reply this email Sin.Jun@tom.com
Then we will send payment instructions.
BUYUNLOCKCODE is being distributed through Trojan horses better known as a type of malicious software, or malware. They use the same method of infiltration that the Greek army used: making you believe they are a benign offering and asking you to invite them (i.e. install them) in and then attacking your computer from within. Very often they masquerade as legitimate program updates or utilities.
Trojan Horse malware, for all intents and purposes, appears to be a program that is useful – and non-threatening. It might be disguised as a game, or, particularly worryingly, as anti-virus or anti-malware software. Trojans often draw your attention to them through the use of a pop up window or via an email. Without thinking too much about it, you'll click on this pop up or on a link or attachment in the email, triggering the BUYUNLOCKCODE virus and giving it access to your PC's operating system. Once installed, it will scan your computer for files with certain file extensions and then encrypt them one by one. All the encrypted files have ".encoded.yourid" at the end of the file, so it's pretty easy to tell whether the file is encrypted or not.
What is more, this malware has a number of unpleasant traits: it is often hard at work behind the scenes monitoring which websites you visit and your browsing habits, and they also have a penchant for collecting your personal data. It does this by logging your keystrokes, giving them immediate access to your passwords, correspondence and online banking details. Some Trojan malware is also able to steal data from your hard drive.
Yet this particular malware has been designed not for fraudulent purposes but with the sole aim of causing chaos on your computer. They can modify your operating system and also corrupt or delete files. And even more frightening is the ability of some variants of BUYUNLOCKCODE to download additional malware causing an absolute nightmare for you and your computer as it is attacked from all angles.
So how can you defend yourself from this scourge of the Internet? A lot of Trojan Horses utilize Windows' .exe file extension so refrain from running these files unless you're 100% sure that they have come from a trustworthy source. Naturally you also want to be running your anti-malware program on a frequent basis – and make sure it is always the latest version too. Stay safe and alert and stay Trojan Horse free.
So what should you do your files have been encrypted? Easy to say, but try not to panic and most definitely do not pay any money unless the encrypted files are very important and you can't afford to lose them. If the encrypted files are not very important or you don't have money to pay the ransom, you can remove try to restore your files (at least some of them) using Shadow Explorer and specialized tools listed below. Please note that even of you decide to pay the ransom there's really no guarantee that scammers will recover your files.
If you have any questions, please leave a comment below. Last, but not least, if there's anything you think I should add or correct, please let me know. It might be a pain but the issue needs to be dealt with – and the way to do it is by not giving in, not paying up and not letting the attackers win.
Written by Michael Kaur, http://delmalware.blogspot.com
Step 1: Removing BUYUNLOCKCODE and related malware:
Before restoring your files from shadow copies, make sure BUYUNLOCKCODE is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by BUYUNLOCKCODE virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
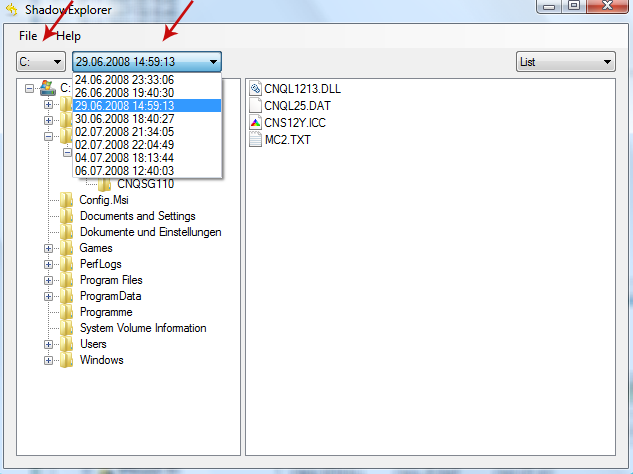
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
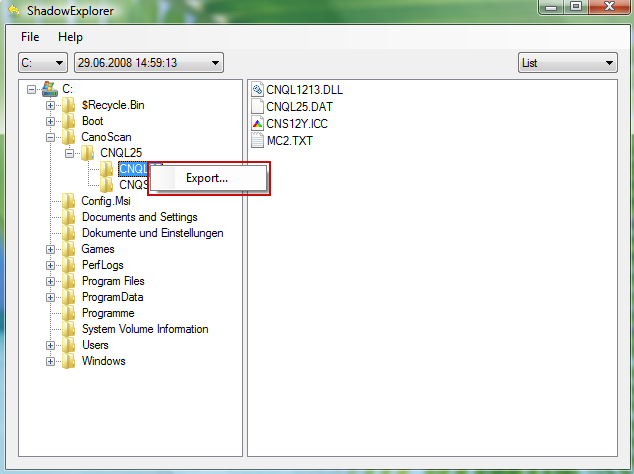
Hopefully, this will help you to restore all encrypted files or at least some of them.

