KEYHolder
YOUR PERSONAL FILES ARE ENCRYPTED
All files including videos, photos and documents on your computer are encrypted.
File Decryption costs ~ $500.
In order to decrypt the files, you need to perform the following steps:
1. You should download and install this browser: http://www.torproject.org/projects/torbrowser.html.en
2. After installation, run the browser and enter the address: mwyigd4n52mkbyhe.onion
3. Follow the instructions on the web-site.
We remind you that the sooner you do, the more chances are left to recover the files.
Guaranteed recovery is provided within 10 days.
As you can see, cyber crooks want you to install Tor web browser go to their website and follow the instructions on how to pay the ransom. One thing is for sure, there can't be any guaranteed recovery as they say at the end of the text. They may give you a decryption program and they may not. I wouldn't recommend paying the ransom unless you absolutely must. You don't have backups, you can't run Windows restore and your files are very important. But if that's not a big problem and you can live without those files, then don't send money to cyber crooks. Just remove KEYHolder and related malware from your computer and next time make sure you have backups. KEYHolder is usually installed by Trojans. Trojan Horse malware fools you into thinking it's harmless, gets you to install it yourself, and then causes untold damage to your computer from inside.
KEYHolder is designed for one reason and one reason alone: to do damage and steal money. It will corrupt your files, data and operating system or hard drive, and they can put your computer's security at risk by allowing an unscrupulous third party person to access your computer through the Internet. Please note this this ransom virus often comes bundled with These Trojans that facilitate the opening of a portal on your operating system through which this person will enter and connect to your device. This gives them the frightening ability to watch what you're doing when you're online from behind the scenes. They also have the power to modify your files - and even delete them if they so choose. Some Trojans also install something called a keylogger which monitors which keys you're hitting, thereby giving them access to your personal data, communications, passwords, online banking details and anything else you can think of. So, not only you need to remove this ransom virus but also make sure that there are no other malware installed on your computer.
Normally KEYHolder is spread through email attachments but sometimes it uses instant messaging applications, peer-to-peer file sharing, or pop-up windows that look like legitimate program upgrade reminders to infiltrate your PC. And to do that, the creator of the ransom virus must first con you into thinking that this attachment is something you really want to open or this upgrade or new program is something you really can't afford not to download.
How to protect yourself from KEYHolde? There a few sensible things you can do: install a good antivirus program and run it regularly, don't open emails from sources you don't know, don't download programs without first checking out what they are online, and update Windows often so you know you have the latest security patches installed. What is more, create backups regularly. I know it's boring and time consuming task but it's actually the most effective way of keeping your files safe.
To remove this virus from your computer and restore at least some of encrypted files, please follow the removal guide below. If you have any questions, please leave a comment below. Last, but not least, if there's anything you think I should add or correct, please let me know. It might be a pain but the issue needs to be dealt with – and the way to do it is by not giving in, not paying up and not letting the attackers win.
Written by Michael Kaur, http://delmalware.blogspot.com
Step 1: Removing KEYHolder and related malware:
Before restoring your files from shadow copies, make sure KEYHolder is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
Important! If you can't download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by KEYHolder virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
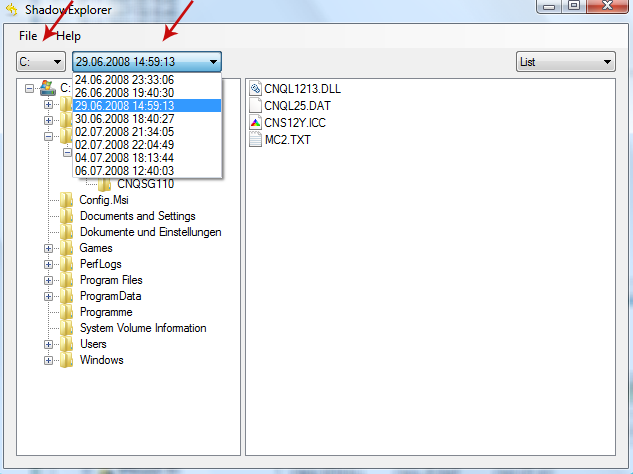
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
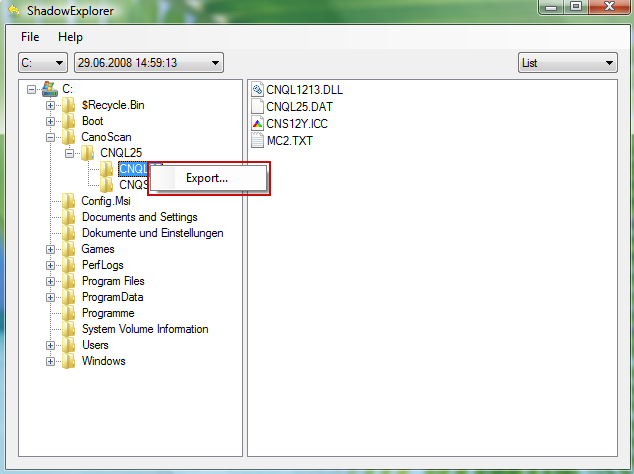
Hopefully, this will help you to restore all encrypted files or at least some of them.

