And one of these maleficent online nightmares is something which is not normally as well known as some of its stable mates, and that is a crypto virus or crypto malware. But just because it's not as widely known as adware, spyware or Trojan Horses that is definitely not a reason to ignore it and hope that crypto virus won't affect you – because if it does, you will certainly know about it. It's a rising malware threat with more and more variations of the Crypto family of viruses. VaultCrypt, TeslaCrypt, CTB-Locker, CryptoWall, KEYHolder, CryptoLocker are only a few examples of cryto viruses that encrypt your files and then demand money from you.
What is a crypto virus?
It is extremely unpleasant. So what can it do to you – and how does it do it? And, more importantly how do you prevent your computer from being infected by it?
Cryto viruses are spread in a number of different ways. It may come in an email attachment, or in a link sent via an instant messenger chat window. You may be unfortunate enough to download a software program which has been infected by it or visit a website that was compromised by it. When you look at it that way, you can see that you really are at risk every time you turn on your computer and connect to the internet. Therefore exercising extreme caution when opening email attachments or clicking on links – no matter whether you know the sender – is key. For all you know Uncle Ted could have had his email hacked or your coworker Pete had his chat app compromised. What is more, cryptoviruses are often backdoor Trojan Horses. These sinister Trojans enable a third party to take control of your computer remotely - turning your machine into something called a Zombie PC. That means that cyber criminals are now able to send, receive or delete files, display data and even reboot your PC. They can also steal your passwords and other important information. So, usually it's not just a ransomware infection that renders your files inaccessible but it can also leave your computer wide open to malware attacks.
What does it do?
It won't take long for you to realize if you're the victim of a crypto virus. The malware's MO is to 'hijack' or 'kidnap' your files, render them inaccessible and then demand money – i.e. a ransom - from you in order to release them. The kidnapper will send you an email or display a pop up window on your screen that demands a certain amount of money. It is then promised that upon payment, you will be sent a code that will allow you to recover, or unlock, your documents. Take the word 'promise' with a huge pinch of salt however, for promises are easily broken and you may well have paid your data's ransom only to find you're no closer to retrieving your files. Ransom viruses use different encryption and decryption methods. The most widespread ransomware CryptoWall 3.0 uses the RSA-2048 cryptosystem. Other cryptoviruses use either RSA-2048 or modified/combined cryptosystems to encrypt your files. Cyber criminals usually accept Bitcoin payments and sometimes prepaid cards.
Ransomware scare tactics
In order to try and convince you into paying for your release code, many crypto viruses also employ a number of brutal scare tactics. These can include pretending that the 'kidnapper' is a law enforcement agency or the FBI (depending on which country you are in) and insisting that your PC has been locked or a file held as it contains illegal data, or that you have been caught downloading illegal programs or software. Telling you that by not paying the ransom by a certain deadline, will render the code forever useless s another method used.
Avoid the horrors of a crypto virus by installing the latest version of a reputable anti-virus software today. Keeping Windows updated too is crucial as this will ensure that you have the latest versions of security patches. Finally, you know it, but are you still guilty of it? Don't download unknown programs and never open emails or attachments from senders you don't recognize. And last, but not least, backup your files! Having backups in place will save you headaches and time. If you have any questions, please leave a comment below. To remove crypto virus, please follow the steps in the removal guide below. Good luck and be safe online!
Written by Michael Kaur, http://delmalware.blogspot.com
Step 1: Removing Crypto virus and related malware:
Before restoring your files from shadow copies, make sure crypto virus is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by Crypto virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
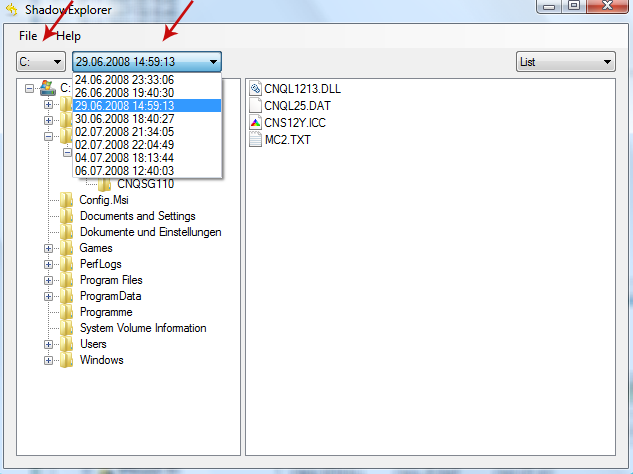
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
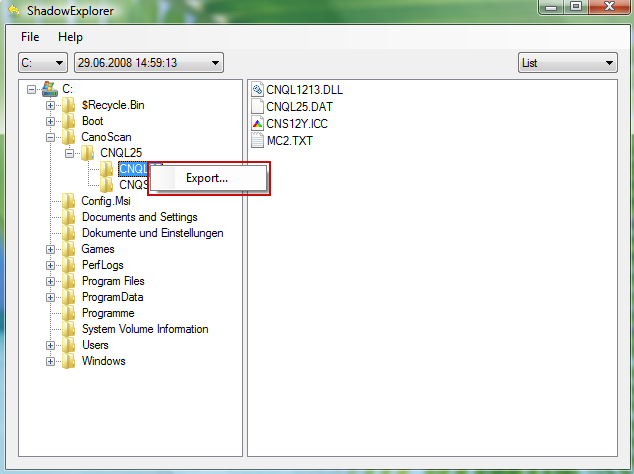
Hopefully, this will help you to restore all encrypted files or at least some of them.

