So it makes sense that as cyber crime grows, we too should take steps to combat it and protect our identities, our privacy and our bank accounts from attacks that can often cause untold pain, hassle and damage.
Just one of the many types of malware to look out for: TeslaCrypt ransomware
One of the most potentially deceptive – and dangerous – malware programs is TeslaCrypt. Unlike some malicious software this is not designed to show you pop-up adverts or redirect your Internet searches; it has a far more financially driven motive in mind than that. No, ransomware isn't interested in your website traffic – it wants your cold hard cash. And if it can scare you in the process, then so much the better!
How can TeslaCrypt affect you?
As the name suggests, ransomware is a program which kidnaps something and holds it to ransom: in this case files on your computer. Yes, physical kidnapping is not the only thing we need to watch out for (although if you’re like me the chances of your files being cyber kidnapped are far higher than being actually kidnapped in person!) But still, let's not make light of this because having your computer hijacked is a definite nightmare in its own way too.
In simple terms, TeslaCrypt will infect your PC, 'kidnap' – i.e. encrypt - your files, and then demand that you pay a ransom for them to be 'released'. It scans your computer for files with .7z, .rar, .m4a, wb2, .rtf, .wpd, .dxg, .xf, .dwg, docm, .docx, .doc, .odb and many other extensions. It does encrypt your files with AES encryption algorithm and at least for know there's really know way to decrypt them without a unique decryption key. One installed, the ransom Trojan will change your Desktop wallpaper to a ransom note and create another ransom note called HELP_TO_DECRYPT_YOUR_FILES.txt on your desktop. Here's how it reads:
v4
Your personal files are encrypted!
Your files have been safely encrypted on this PC: photos, videos, documents, etc. Click "Show Encrypted Files" button to view a complete list on encrypted files, and you can personally verify this.
Encryption was produced using a unique public key RSA-2048 generated for this computer. To decrypt files you need to obtain the private key.
As you can see, tt says you have 3 days to make payment. It also allows you to decrypt one file for free, just like the CryptoWall 3.0 virus. HELP_TO_DECRYPT_YOUR_FILES.txt contains the same information. In reality releasing your files means sending you a key or code to decrypt the file. Payment is made either by digital currency such as Bitcoins or by a PayPal My Cash card which you need to purchase. Usually, users of malware steer clear of taking credit card payments or using online payment platforms such as PayPal as these are too easily traceable but not this time.
How does this ransomware infect your computer?
TeslaCrypt attacks and installs itself on your PC either through an infected email attachment, or through a drive-by installation – meaning you have picked it up from a compromised website or program.
What should you do if you've been infected by TeslaCrypt? Should you pay the fine?
In a word, no! There are two reasons for this: a) you're only encouraging further criminal activity and b) how do you know that you'll receive the decryption key anyway? If the encrypted files are not very important or you don't have money to pay the ransom, you can remove try to restore your files (at least some of them) using Shadow Explorer and specialized tools listed below. Please note that even of you decide to pay the ransom there's really no guarantee that cyber crooks will send you the private key and you will be able to decrypt your files. If you have any questions, please leave a comment below. If there's anything you think I should add or correct, please let me know. And now you're done reading this, may we suggest that you back up all your files onto an external hard drive NOW. That way if you are unlucky enough to fall victim to ransomware, you'll be able to simply wipe clean your internal disk drive and replace it with up to date data.
Written by Michael Kaur, http://delmalware.blogspot.com
Step 1: Removing TeslaCrypt and related malware:
Before restoring your files from shadow copies, make sure TeslaCrypt is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
Important! If you can't download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by TeslaCrypt virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Try the TeslaCrypt Decryption Tool by Cisco. Download TeslaDecrypt tool and run it.
Method 4: Using the Shadow Volume Copies:
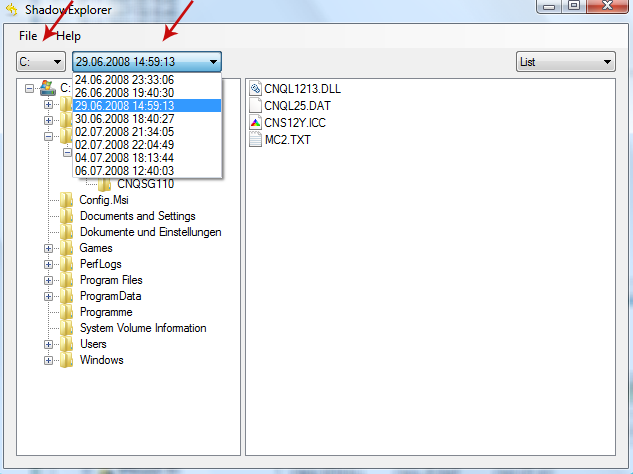
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
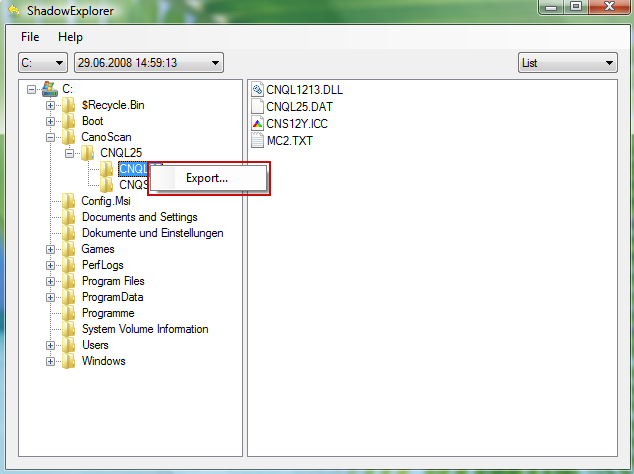
Hopefully, this will help you to restore all encrypted files or at least some of them.


