Additional files on how to pay the ransom and get your files back were created on infected computers as well. HELP_DECRYPT.HTML opens your web browser and displays all the information about the virus, encryption methods and payment options. HELP_DECRYPT.PNG contains more information about the virus. HELP_DECRYPT.TXT shows the same information as the previous file just in plain text. HELP_DECRYPT.URL loads your default browser and display the CryptoWall 3.0 Decrypt Service when you login to Windows. These are the main changes. Everything else is pretty much the same. You don't have to be an academic or a brain surgeon to know that as someone who uses a computer on a regular basis that this ransom virus poses a very real threat to your online safety and most importantly your data. But even if you are aware of this fact, how certain can you be that you're protecting your business, or your personal, data as well as you can be?
No two pieces of malicious software are the same – even the ones that fall under the same category – and as technology, and anti-malware programs become increasingly advance, so too do viruses and malware. Malware developers, hackers and shadowy third parties who pay good money for stolen data are often one step ahead and increasingly use some incredibly sophisticated techniques in an attempt to steal your information or your bank details, or even just to cause computer issues for you – just for fun!
How does the CryptoWall 3.0 virus work? Well, once installed, it starts to encrypt your files in the background and sadly most people do not realize this ransomware virus is on their computer until it displays the ransom note and your files have already been encrypted. The ransom note is a simple HTML file with instructions on how to pay the ransom and get your encryption key. It's not a joke, it's a very serious problem. Here's how the HELP_DECRYPT.HTML reads:
What happened to your files ?
All of your files were protected by a strong encryption with RSA-2048 using CryptoWall 3.0.
More information about the encryption keys using RSA-2048 can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem)
What does this mean ?
This means that the structure and data within your files have been irrevocably changed, you will not be able to work with them, read them or see them, it is the same thing as losing them forever, but with our help, you can restore them.
How did this happen ?
Especially for you, on our server was generated the secret key pair RSA-2048 - public and private.
All your files were encrypted with the public key, which has been transferred to your computer via the Internet.
Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our secret server.
What do I do ?
Alas, if you do not take the necessary measures for the specified time then the conditions for obtaining the private key will be changed.
If you really value your data, then we suggest you do not waste valuable time searching for other solutions because they do not exist.
CryptoWall 3.0 uses the RSA-2048 encryption algorithm to encrypt your files. Cyber crooks don't lie. This has been confirmed by multiple sources. Once your files are encrypted, it deletes the original files and if you don't have back ups there's really not much you can do to get them back. Your last option is to use software that tries to restore files or part of the files from Windows shadow copies. For more information, please read the removal guide below.
Its main goal is to attack and encrypt your personal files that are valuable to you. It encrypts various files not just MS Office documents but also images, audio files and pretty much everything else it finds on your computer. Such viruses are sneaky and stealthy and will install themselves on your computer by pretending to be something that they're really not - i.e. something harmless and useful. They are also distributed via infected websites and fake emails. How ironic is that?
Unfortunately for us, no matter whether you're a home user or you're responsible for the safeguarding of a company network, the ransomware threat is only growing – both in frequency and in terms of sophistication. The previous versions of this virus encrypted more than 5 billions files. So how do you protect yourself against CryptoWall 3.0?
So what should you do your files have been encrypted? Easy to say, but try not to panic and most definitely do not pay any money unless the encrypted files are very important and you can't afford to lose them. If the encrypted files are not very important or you don't have money to pay the ransom, you can remove try to restore your files (at least some of them) using Shadow Explorer and specialized tools listed below. Please note that even of you decide to pay the ransom there's really no guarantee that cyber crooks will recover your files.
If you have any questions, please leave a comment below. Last, but not least, if there's anything you think I should add or correct, please let me know. It might be a pain but the issue needs to be dealt with – and the way to do it is by not giving in, not paying up and not letting the attackers win.
Written by Michael Kaur, http://delmalware.blogspot.com
Step 1: Removing CryptoWall 3.0 and related malware:
Before restoring your files from shadow copies, make sure CryptoWall 3.0 is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by CryptoWall 3.0 virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
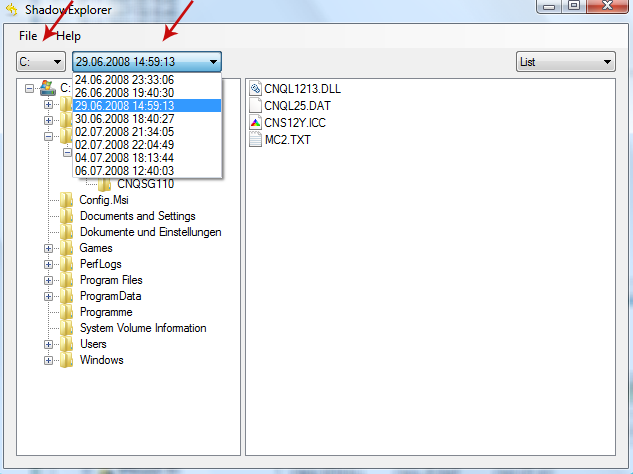
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
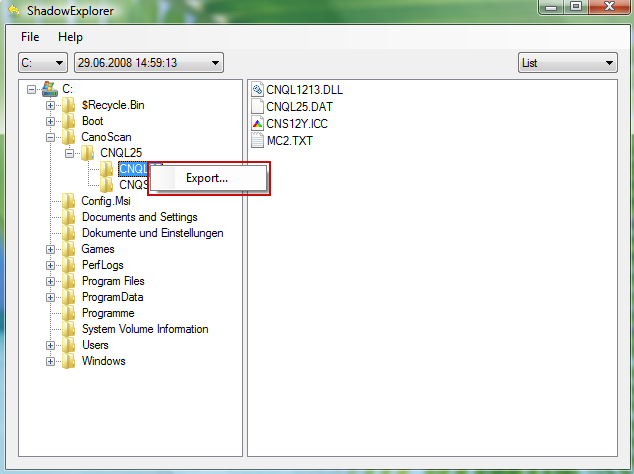
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
Hopefully, this will help you to restore all encrypted files or at least some of them.

