There are more than enough different types of malicious software out there to keep us on our toes, but one of the most unpleasant ones is ransomware which seems to rear its ugly head in fits and starts, rather than being a constant on the malware landscape. However just because it appears to come and go is not reason to ignore it for ransomware is something that can cause untold stress, both on you and on your bank account, if you are not careful.
What exactly is TeslaCrypt ransomware?
The name probably gives it away, or at least holds a clue as to what this particular Internet based menace can do and how it operates. To cut a long story short, ransomware infests your computer, kidnaps one or more of your files, changes file extension to .ecc, holds them hostage – and then, as a natural conclusion, demands a ransom from you to let them go free.
How does it infect my PC?
As with most types of computer virus or malware, ransomware infects you via email carrying an infected attachment or link. It can also disseminate itself through other programs or it may employ a technique called a drive-by installation – this is when you visit a website that has been compromised.
You may notice that something is amiss on your computer when you suddenly find that you can't access a particular file or document, when you receive a ransom note – i.e. an email - or you are shown a screen or pop-up window alerting you. Usually these emails or alerts will appear to have been sent by a reputable organization such as the FBI or other national law enforcement agency. This of course would have the majority of us shocked into stunned silence (or possibly letting slip a few choice curse words!)
But what am I "guilty" of?
The email or warning will tell you that you have infringed some sort of serious law: maybe you've been "caught" looking at some dubious x-rated content or downloading pirated software or movies, for example.
Then, still pretending that a genuine federal or law agency were behind the message, you will then be shown how much you are being penalized and the amount of the fine you need to pay to atone for your "wrongdoing". But don't worry, this untoward third party will make it nice and easy for you to pay – this will either be by using an (untraceable) pre-paid card or Bitcoins, the digital currency.
Should I pay the fine?
No. Do not encourage these online scammers; no reputable law enforcement agency uses these tactics. If you have a recent backup, wipe your hard disk and reinstall your files. If you don't, try Shadow Explorer program or search your computer for previous versions of files. If you are lucky enough you may find files that were not encrypted and renamed to .ecc. But before restoring your files, please remove the ransomware and related malware files from your computer. Otherwise, you will simply waste your time. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://delmalware.blogspot.com
Step 1: Removing TeslaCrypt and related malware:
Before restoring your files from shadow copies, make sure TeslaCrypt is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
Important! If you can't download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by TeslaCrypt virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Try the TeslaCrypt Decryption Tool by Cisco. Download TeslaDecrypt tool and run it.
Method 4: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
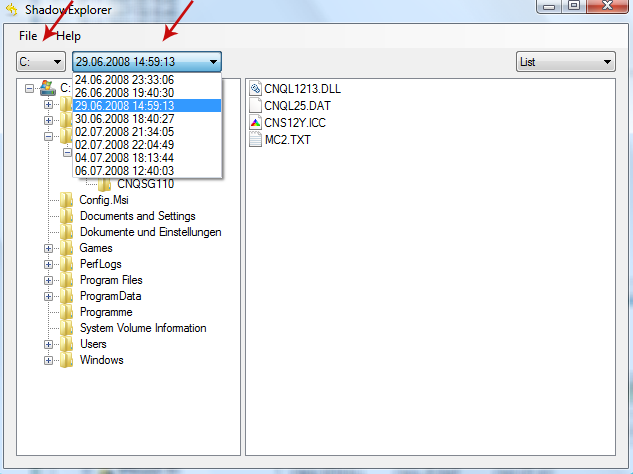
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
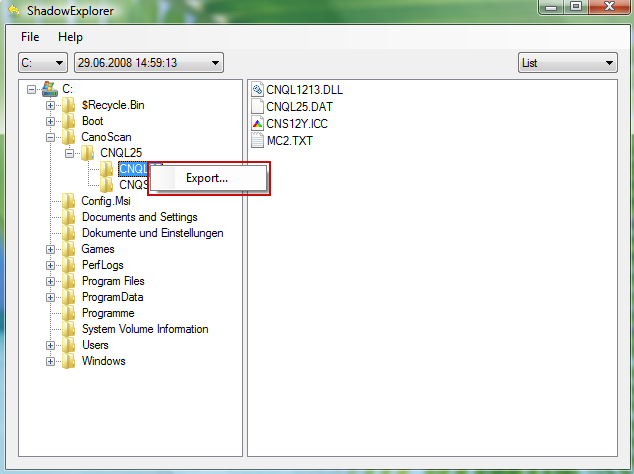
Hopefully, this will help you to restore all encrypted files or at least some of them.

