What is ransom Trojan malware?
Ransom Trojans are the most commonly found type of malware on the Internet – which is unfortunate because they are also one of the nastiest. They are a serious threat to your computer's security and they have a nasty habit of encrypting your files. Generally speaking they are used to extract money from you or to defraud you and they can do a lot of irretrievable damage. This particular ransom Trojan encrypts pretty much every file on your computer. It simply scans your computer for files, encrypts them and gives random names to each file ending with the XTBL file extension. Then, it creates at least 10 text files with instructions on how to get your files back. It also adds a new background image with warning that your files were encrypted and that you have to read README.txt files for more information. Here's how it looks:
And here's how the README.txt reads:
Ваши файлы были зашифрованы.
Чтобы расшифровать их, Вам необходимо отправить код:
[edited]
на электронный адрес deshifrator01@gmail.com или deshifrovka@india.com.
Далее вы получите все необходимые инструкции.
Попытки расшифровать самостоятельно не приведут ни к чему, кроме безвозвратной потери информации.
All the important files on your computer were encrypted.
To decrypt the files you should send the following code:
[edited]
to e-mail address deshifrator01@gmail.com or deshifrovka@india.com.
Then you will receive all necessary instructions.
All the attempts of decryption by yourself will result only in irrevocable loss of your data.
As you can see, cyber crooks provide the same information in two languages: English and Russian. It probably means that this ransomware campaign targets not only English speaking countries but also others that understand Russian. Each victim gets a unique code that must be emailed to either deshifrator01@gmail.com or deshifrovka@india.com. I'm pretty sure that they change email address quite often, so don't be surprised if yours are different. Cyber crooks say that they will send you all necessary information by email and that all attempts to decrypt your files will result in data loss. I haven't tried to contact them, so I can't say whether it's true or not. What I can confirm is that this ransom Trojan does encrypt files. My guess is that cyber crooks ask to pay the ransom which could be $300, $500 or even more in order to get a decryption tool and decrypt your files. That's how ransomware usually works.
Here's how encrypted files look like:
How does ransom Trojan malware get its name?
Trojan Horse malware takes its name from the ancient Greek fable (or true story?!) in which Greece defeated their enemies in the Trojan War by building a gigantic, hollow wooden horse and hiding their soldiers inside it. They wheeled the horse to the gates of the city and pretended it was a peace offering to the people of Troy. In reality, of course, it was merely a tactical attempt to infiltrate the city and attack it from the inside. And that is precisely what they did, winning the war.
And that is precisely how ransom Trojan malware works too. It is a malicious computer program that has been designed to look as if it is innocent. So when you think you are downloading a game, the latest episode of your favorite TV show shared in a peer to peer file, or even an anti-virus program, you could in fact be downloading and installing malware instead. And it's usually a combination of different Trojans. In my case, it was Worm.Korron, Trojan.Agent.XN and Trojan.Packed.28357. The last one runs from the %Temp% folder and downloads orher malware files onto your computer. It's very important to remove all malware from your computer before trying to restore your files or use any file decrytion tools.
Traits of ransom Trojan Horse
As well as causing security breaches on your operating system and deleting your files (in fact they can erase all the contents contained in your entire system), extremely scarily, they can also give the programmer of the Trojan Horse access to your computer. They will encrypt your files and then turn your PC into something called a zombie computer and use it to attack other users.
So without further ado – here are 2 ways to protect yourself – and your PC – from ransom Trojan Horse malware
- Many ransom Trojans are hidden in email attachments, links in instant messenger chat apps or in shareware and P2P files, however websites are also used to download them onto your machine by use of something called a 'drive by' installation. Any website can be a potential target by a cyber crook – and therefore a potential danger – but the more disreputable the site (pornography or gambling sites for example) the bigger the danger.
- Back up your files on a regular basis and keep files on a hard drive, or even on another computer – anywhere safe! Backup twice if you want to doubly ensure your safety. When you have copies of all your files, documents and data you will be able to get back up and running again much quicker than if a ransom Trojan encrypted everything and you had no duplicates.
Written by Michael Kaur, http://delmalware.blogspot.com
Step 1: Removing the ransom Trojan and related malware:
Before restoring your files from shadow copies, make sure the ransomware is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
Important! If you can't download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by ransom Trojan virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
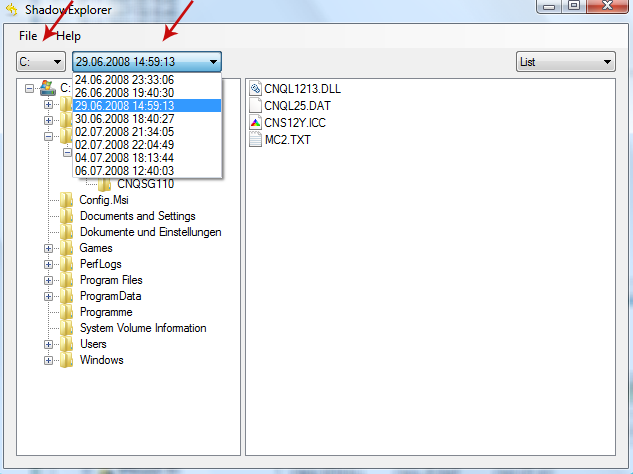
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
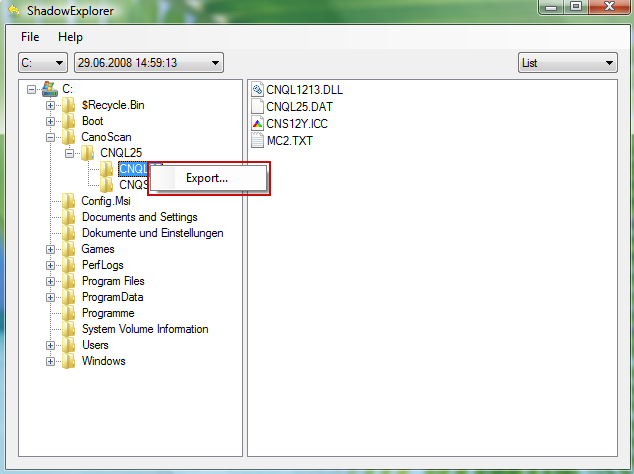
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
Hopefully, this will help you to restore all encrypted files or at least some of them.


