Here's what the Threat Finder v2.4 notifications says. If you got it then it's already too late.
Threat Finder v2.4
Warning! Your personal files are encrypted!
Don't switch off your computer and/or internet, otherwise your key will be disabled
Your important files encryption produced on this computer: photos, videos, documents, etc. Here is a complete list of encrypted files, and you can personally verify this.
Encryption was produced using a unique public key RSA-2048 generated for this computer. To decrypt the files you need to obtain the private key.
The single copy of the private key, which will allow you to decrypt the files, located on a secret server on the Internet, the server will destroy the key after a time specified in this window. After that, nobody and never will be able to restore files.
To obtain the private key for this computer, which will automatically decrypt files, you need to pay 300 USD / 300 EUR / similar amount in another currency.
Any attempt to remove or damage this software will lead to immediate destruction of the private key by the server.
Threat Finder is a type of malware and, unlike adware or spyware, is one whose main purpose is to get you to pay money for your files that were encrypted using RSA 2048 cryptosystem. This threat gets in mostly via infected email attachments and drive-by downloads from infected web sites. It is also being pushed directly to infected computers that belong to certain botnets. It also uses something called social engineering to infect your computer – for example, the cyber crooks might post a link on Facebook or Twitter. You click on this link and the software will download itself on to your PC by exploiting a weak spot in your security. The pop-up window is then utilized as a scare tactic to 'engineer' you into installing, and paying for, the software.
That's not the only way you can find yourself infected however as Threat Finder is installed via a 'drive-by' download. For example, if you have visited a website that has been infected, then by default you too will become a victim. Obviously the key here is to avoid ransomware from installing itself on your computer and fooling you into spending money on a product that either doesn't work – or worse, can do you harm. The best advice is to install reputable security software and make sure it is kept up to date.
So what should you do your files have been encrypted? Easy to say, but try not to panic and most definitely do not pay any money unless the encrypted files are very important and you can't afford to lose them. If the encrypted files are not very important or you don't have money to pay the ransom, you can remove try to restore your files (at least some of them) using Shadow Explorer and specialized tools listed below. Please note that even of you decide to pay the ransom there's really no guarantee that cyber crooks will send you the private key and you will be able to decrypt your files.
If you have any questions, please leave a comment below. Last, but not least, if there's anything you think I should add or correct, please let me know. It might be a pain but the issue needs to be dealt with – and the way to do it is by not giving in, not paying up and not letting the attackers win. Good luck and be safe online!
Written by Michael Kaur, http://delmalware.blogspot.com
Step 1: Removing Threat Finder and related malware:
Before restoring your files from shadow copies, make sure Threat Finder is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
Important! If you can't download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by Threat Finder virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
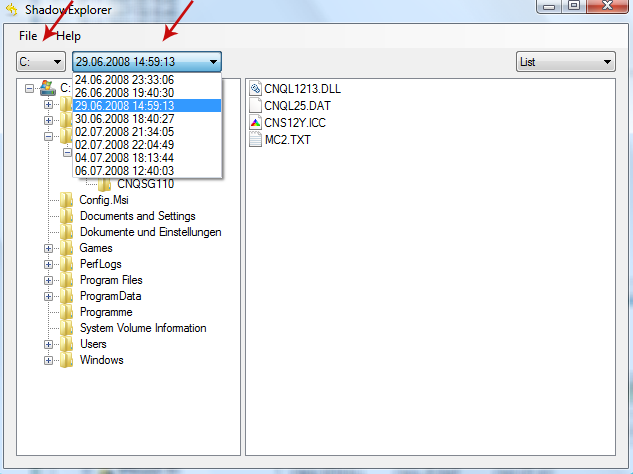
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
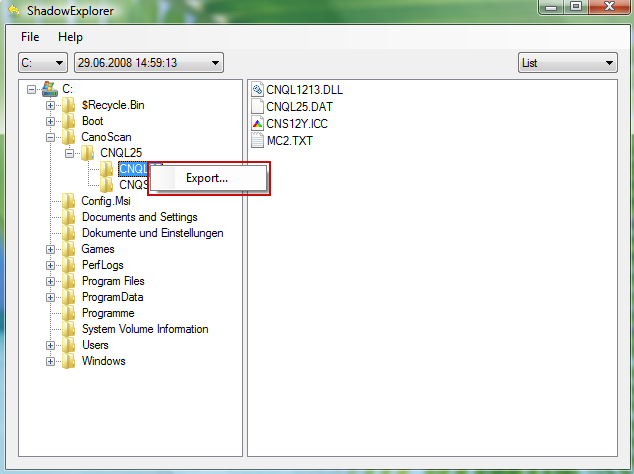
Hopefully, this will help you to restore all encrypted files or at least some of them.

