First of all, if your computer has been hit with this Trojan Horse, chances are it was your fault. Unlikely as it seems, the unfortunate fact is that we often play a part in infecting ourselves when it comes to malware, especially Trojans. And laying the blame at your door is exactly what Trojan Horses are all about. So that a Trojan can worm its way onto your computer you need to install its server function. And for you to install the server function, the Trojan needs to trick you into doing just that.
Once installed, it will change Windows Registry and files so that you will get the This computer was automatically blocked. Reason: Pirated software has been detected. message on every startup. Here's how the fake message reads:
Willful copyright infringement is a federal crime that carries penalties of up to five years in federal prison, a $250,000 fine, forfeiture and restitution (17 U.S.C s.506, 18 U.S.C s.2319)
As a first-time offender you are required by law to pay a fine of 500 CAD
If the fine is not paid within three days, a warrant will be issued for your arrest, which will be forwarded yo your local authorities. You will be charged, fines, convicted for up to 5 years.
How to pay a fine? There are two ways to pay a fine:
1. You can pay the fine online through BitCoin. BitCoin is available nationwide.
2. (Offline Option) You can come to your local courthouse and pay the fine at the 'Cashiers' window.
OK, so the second payment option is absolutely unrealistic. As well as the fact that your files will be lost if you won't pay the fine. And at the bottom of the messages scammers claim that this operation Stop Online Privacy-Project Global 3 is is a coordinated effort by the U.S., Canadian, European, Australian, U.K., New Zealand and other law enforcement agencies across the globe targeting computers with pirated content. It's not true of course but may also reveal what countries are targeted by scammers.
And that is precisely how this type of malware gets its name. You may recall being told the story of Helen of Troy and the Trojan horse when you were at school. Well, our modern day Trojan has more in common with Greek mythology than you might think. Think back to when the ancient Greeks penetrated the city of Troy by hiding their army in the hollow body of a giant wooden horse, presented the horse as a peace offering to their enemies, the Trojans and then attacked the city from within. This too is how today's Trojan Horses operate: they convince you that they are a legitimate program that not only has nothing wrong with them, but are also something desirable or useful.
"Pirated software has been detected." ransom Trojan is often included in spam emails as an attachment. As soon as you click to open this attachment you've allowed the Trojan to install itself on your PC. This is a favored MO of Trojan creators as the malware, unlike viruses, doesn't replicate itself – they can simply send out a mass emailing and then wait for the recipients to do their dirty work for them. Once you have executed and installed the Trojan Horse the server that it is connected to will launch its software each time you log on to your computer.
So why do Trojan Horses employ such underhand tactics? That's because the scammers know that if you knew the damage they could cause you would go out of your way to avoid them. Trojans are malicious and can really cause problems for you and your computer. They can corrupt your data and make your files and programs impossible to open or access.
The good news is that there are things you can do to protect yourself. Firstly, ensure you have a reputable (and up to date) anti-malware program. And it goes without saying that you should never open an email or click on an attachment or link if you don't recognize the sender.
If you have any questions, please leave a comment below. Last, but not least, if there's anything you think I should add or correct, please let me know. It might be a pain but the issue needs to be dealt with – and the way to do it is by not giving in, not paying up and not letting the attackers win. Good luck and be safe online!
Written by Michael Kaur, http://delmalware.blogspot.com
Step 1: Removing "Pirated software has been detected" ransomware and related malware:
Before restoring your files from shadow copies, make sure this ransom Trojan is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. Please reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key.
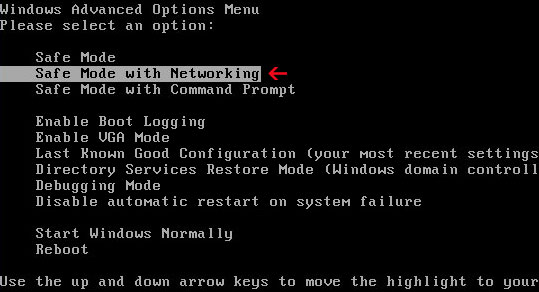
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Then, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by this virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
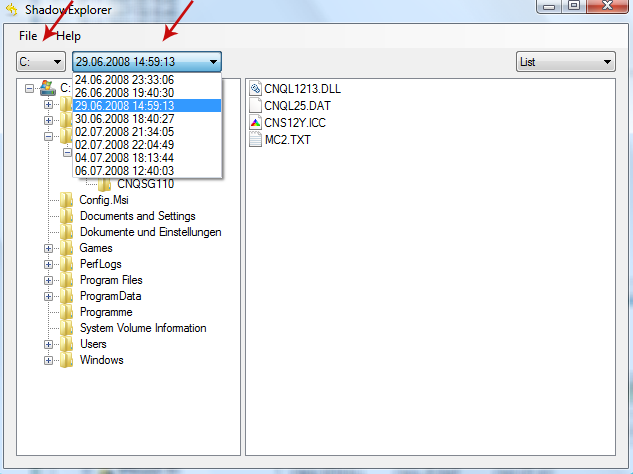
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
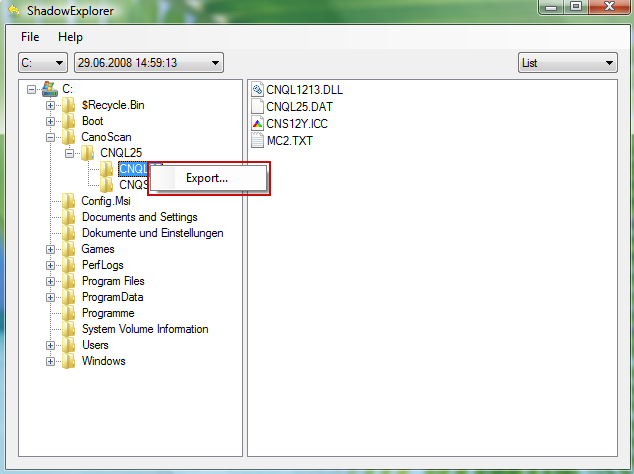
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
Hopefully, this will help you to restore all encrypted files or at least some of them.

